DevSecOps: Secure Software Development Lifecycle (SSDLC)




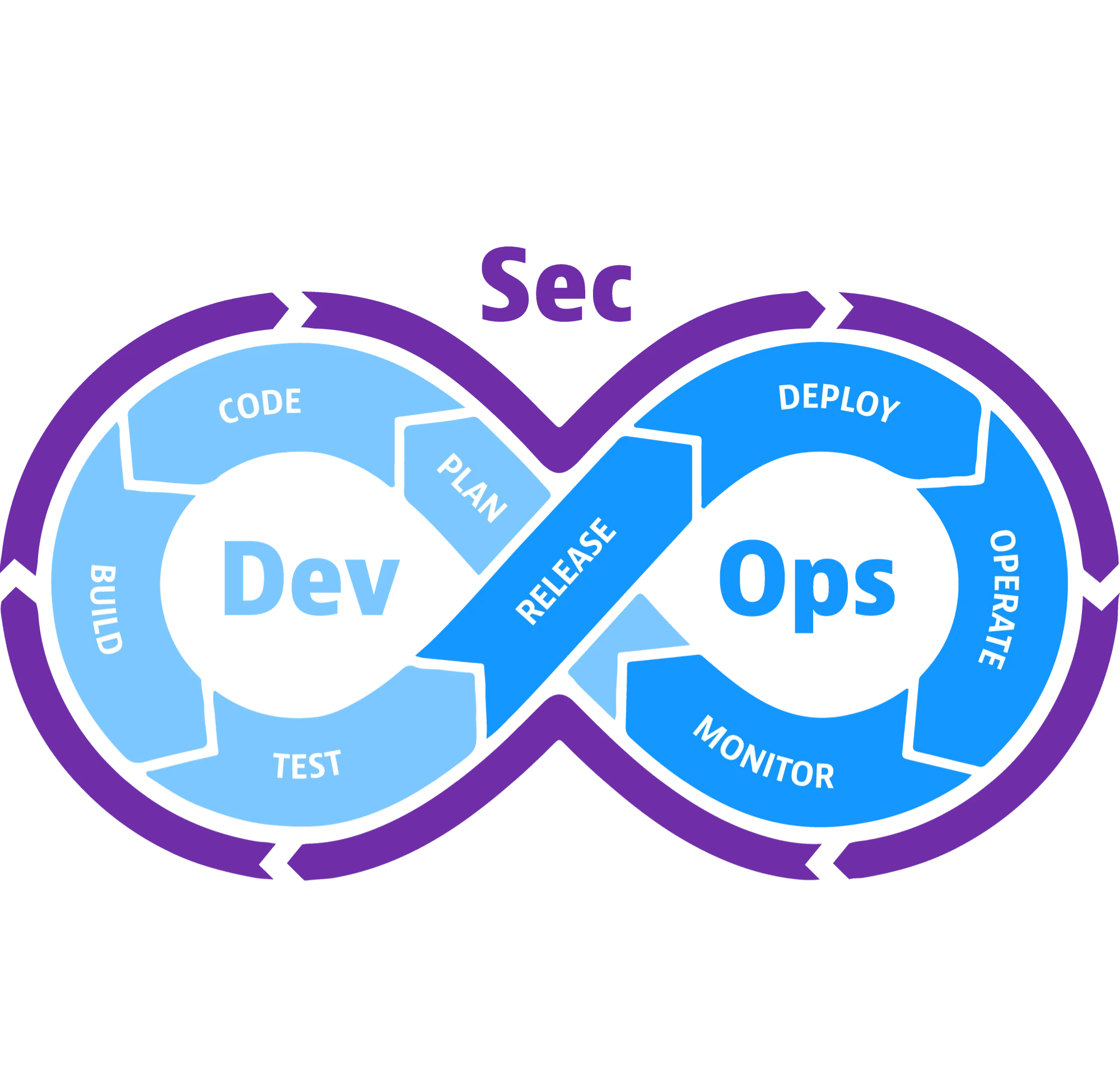
At Cloudnitio, we specialize in the integration of DevSecOps, also known as Secure DevOps, which enhances the conventional DevOps approach by embedding security measures at various phases of the DevOps cycle.
Security risks can arise at any stage of the development lifecycle. During the design phase, it is crucial to create a design that does not provide easy access points for attackers to the workload, its data, or other business assets. Threat modeling can be used to identify potential security issues based on the design.
In the coding phase, the focus should be on writing secure code that does not allow attackers to take control of the application and perform unauthorized actions. Developers should also ensure they work in a secure environment. Secure coding practices should be followed to avoid common coding vulnerabilities. Static Application Security Testing (SAST) can be used at this stage to help you achieve that.
The build and deployment phase involves continuous integration and continuous deployment (CI/CD) processes. These processes should be secure enough to prevent unauthorized users from altering the code and potentially compromising it. Dynamic Application Security Testing (DAST) can be used after the application is deployed, to test the running application for vulnerabilities.
When the app is running, it is important to follow security best practices to prevent attackers from compromising the workload. Regular security audits and monitoring should be performed to detect any runtime anomalies or breaches.
Lastly, all these stages should adhere to Zero Trust principles, which involve assuming a breach, verifying trust explicitly, and granting the least privilege necessary. This approach helps maintain a high level of security throughout the development lifecycle.
Beyond SAST and DAST, there are other testing strategies such as Interactive Application Security Testing (IAST) and Software Composition Analysis (SCA).
IAST merges the techniques of SAST and DAST to identify a broader spectrum of security vulnerabilities.
SCA is instrumental in creating an inventory of all third-party commercial and open-source components utilized in your applications.
While there are numerous security controls to apply throughout the development lifecycle, the advent of automation has made their implementation much more manageable. Automation tools can be used to apply these controls efficiently and consistently, reducing the risk of human error. This not only ensures a high level of security but also allows the development team to maintain their productivity. The automated processes run in the background, requiring minimal intervention from the team, thus saving valuable time. Therefore, automation is a key component in maintaining security without compromising on team's productivity or time.
There are many advantages of integrating security into DevOps practices, including:
This is just one example of the projects we have successfully implemented for our clients, helping them establish a robust DevSecOps practice within their teams and organizations.
We have our sample projects available to showcase to you how we can help you to implement a DevSecOps practice in your organization. You can contact us and schedule a meeting to discuss your requirements and constraints, and we will be happy to help you to achieve your goals.